What is the Security Breach chapter used for?
Proposal Kit Professional Bundle adds more design themes, all six Contract Packs,
a project management library, and Expert Edition software.

Illustration of Proposal Pack Elegant #4
We include this Security Breach chapter template in every Proposal Pack, along with thousands more. You assemble this chapter with others in various combinations to create custom-tailored business proposals, plans, reports, and other documents. Proposal Packs apply custom visual designs to the templates, giving the final documents a consistent professional finish.
 DOWNLOADABLE, ONE-TIME COST, NO SUBSCRIPTION FEES
DOWNLOADABLE, ONE-TIME COST, NO SUBSCRIPTION FEES
Overview of the Security Breach Chapter
The Security Breach chapter is an important part of a proposal document, especially in contexts where the security and confidentiality of information are paramount. This chapter serves as a detailed explanation of any security incidents that might have impacted the organization, explaining their nature, detection, and the responses enacted. Its presence in a proposal reassures the reader that the proposer is transparent about past vulnerabilities and is proactive about future threats.
How is the Security Breach Chapter Used?
When used in a business proposal, the Security Breach chapter is used to address specific incidents of security failures that could affect the project or the organization being proposed as a service provider. This chapter helps in building trust by openly discussing past issues and illustrating steps the organization has taken to mitigate such risks going forward. It sets the stage for explaining enhancements or changes in security measures being proposed to prevent future breaches.
What is Included in the Security Breach Chapter?
The Security Breach chapter typically includes:
- A detailed description of the breach, including what happened and when.
- The scope of the breach and the data or operations affected.
- The measures taken immediately after the breach was discovered.
- An analysis of why the breach happened, highlighting any vulnerabilities.
- Steps the organization has taken or plans to take to strengthen security and ensure such breaches do not recur.
Use Case Examples for the Security Breach Chapter
This chapter can be adapted to a wide range of proposals connected to different industries. Some examples include:
- Web Development Proposals: Describing previous security breaches in web applications and the measures taken to secure websites in the future.
- IT Services Proposals: Outlining incidents of data loss or system hacks and subsequent upgrades in IT security protocols.
- Software Solutions Proposals: Detailing software vulnerabilities that were exploited and the patches or software updates that followed.
- Hardware Supply Proposals: Citing instances of physical security breaches in hardware storage facilities and the implementation of improved security systems.
- Technical Consulting Proposals: Providing analyses of security breaches in systems and networks and recommending technical safeguards.
- Security Services Proposals: Discussing past failures in surveillance or monitoring services and the introduction of more advanced technology.
- Protection Services Proposals: Highlighting lapses in personal or asset protection services and the training or resources added to enhance safety.
- Safety Equipment Proposals: Reflecting on product failures that led to security breaches and the improved design features to prevent such issues.
Key Takeaways
- The Security Breach chapter is important for proposals where security and trust are critical.
- It provides a narrative of past breaches, their impact, and the corrective actions taken.
- This chapter is and can be tailored to a variety of industries from IT to physical security.
- Transparency in discussing past security issues helps build trust with potential clients or partners.
- By including this chapter, organizations demonstrate accountability and commitment to continuous improvement in security practices.

Illustration of Proposal Pack Infrastructure #3
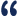 What Our Clients Say
What Our Clients SayThis program is very easy to use and is written layman’s terms. There are no difficult legal terms to figure out. I like this program and recommend it to anyone who wants to create a quick document for business purposes."
E. P. Willard Business Systems Inc.
 4.7 stars, based on 845 reviews
4.7 stars, based on 845 reviewsRelated Chapters
- Emergency Response Plan
- Evacuation Plan
- Security Plan
- Rapid Response
- First Response
- Countermeasures
- Counter-terrorism
- Safeguards
- Threat Assessment
- Loss Prevention
- Protective Measures
- Damage Control
- Safety
- Security
- Terrorism
- Site Security
- Escape Routes
- Safety Devices
- Security Devices
- Rescue Systems
- Warning Systems
- Cyber-security
The Security Breach chapter and other chapters are integrated into a Word document as illustrated here in the Proposal Pack Events #5 design theme. There are hundreds of design themes available, and every design theme includes the Security Breach chapter template.
A proper business proposal will include multiple chapters. This chapter is just one of many you can build into your proposal. We include the complete fill-in-the-blank template in our Proposal Pack template collections. We also include a library of sample proposals illustrating how companies in different industries, both large and small, have written proposals using our Proposal Packs. This template will show you how to write the Security Breach.
We include a chapter library for you to build from based on your needs. All proposals are different and have different needs and goals. Pick the chapters from our collection and organize them as needed for your proposal.
Using the Proposal Pack template library, you can create any business proposal, report, study, plan, or document.
 Ian Lauder has been helping businesses write their proposals and contracts for two decades. Ian is the owner and founder of Proposal Kit, one of the original sources of business proposal and contract software products started in 1997.
Ian Lauder has been helping businesses write their proposals and contracts for two decades. Ian is the owner and founder of Proposal Kit, one of the original sources of business proposal and contract software products started in 1997.By Ian Lauder
 Published by Proposal Kit, Inc.
Published by Proposal Kit, Inc.


 Cart
Cart
 Facebook
Facebook YouTube
YouTube X
X Search Site
Search Site